Welcome to the Edge Security: Lessons from a Journey That Could Be Yours
Welcome to a story about edge computing, where innovation collides with data security and regulatory compliance challenges. Organizations like Lil' Big Mining Co. are at the forefront of this evolving landscape, leveraging existing and new use cases yet to be uncovered. However, a significant challenge they face is securing this new frontier while meeting stringent compliance standards. Our journey with Lil' Big Mining Co. highlights their strategic decision to pursue SOC2 certification, a critical step in addressing these challenges.
Why SOC2 Certification?
For Little Big Mining Co., the pursuit of SOC2 certification is not merely about adhering to an industry benchmark. It’s a strategic decision driven by a multitude of factors:
- Building Trust with Stakeholders: SOC2 certification signals to customers, investors, and partners that Lil' Big Mining Co. is committed to maintaining high security and data protection standards.
- Enhancing Security Posture: The SOC2 framework provides a comprehensive blueprint for managing data security, a critical aspect for companies dealing with sensitive telemetry data from remote locations. By aligning their security practices with SOC2 requirements, Little Big Mining Co. aims to bolster their defenses against cyber threats.
- Facilitating Business Growth: SOC2 certification is often a prerequisite for doing business in many sectors, making it a strategic asset that can open new doors and opportunities.
- Streamlining Compliance Efforts: The SOC2 certification process helps organizations identify and mitigate vulnerabilities, creating a more resilient infrastructure. For Little Big Mining Co., this means not just meeting current compliance requirements but also laying a foundation that can adapt to future regulatory changes.
With these motivations in mind, Little Big Mining Co. embarks on the journey towards SOC2 certification, navigating the complexities of edge computing security and compliance. This blog post will delve into the intricacies of this process, exploring the challenges, triumphs, and strategic decisions that define their journey.
Introduction: The Challenge at the Edge
The demand for immediate connectivity and data access has never been higher. Edge computing has emerged as a solution, processing data closer to its source. Little Big Mining Co. represents companies at this digital frontier, aiming to collect telemetry data from equipment across remote locations. These areas, characterized by limited connectivity and bandwidth, present unique challenges. However, the insights gleaned from this data—monitoring equipment performance, analyzing samples, and optimizing maintenance—are invaluable.
To overcome these challenges, Little Big Mining Co. plans to deploy local Kubernetes clusters at remote sites, turning them into data processing hubs. This strategy, while innovative, introduces significant security concerns that need addressing to protect data as it moves from these remote sites back to central offices.
Navigating Compliance: SOC 2 and NIST CSF
The journey into edge computing brings Little Big Mining Co. face-to-face with the challenge of regulatory compliance. Standards like SOC 2 and NIST CSF are critical in this context, serving as frameworks to ensure data security and system integrity. Achieving compliance is a strategic necessity for securing operations and building trust.
Understanding SOC 2 Controls
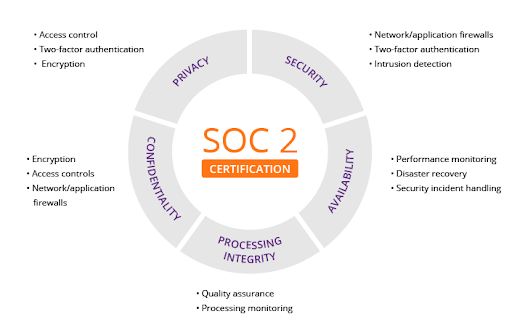
To align with SOC 2 requirements, Little Big Mining Co. adheres to specific criteria addressing security, availability, processing integrity, confidentiality, and privacy. These criteria guide their efforts to protect systems and data effectively.
- Security: Ensuring that data and systems are protected against unauthorized access, misuse, and breaches.
- Availability: Ensuring that systems and resources are available and accessible to authorized users when needed.
- Processing Integrity: Ensuring that data processing is accurate, complete, and timely to maintain the integrity of information and operations.
- Confidentiality: Ensuring that sensitive data is protected from unauthorized disclosure or access.
- Privacy: Ensuring compliance with privacy laws and regulations, protecting personal information, and providing transparency and control over data usage.
Understanding these SOC 2 controls lays the foundation for exploring their alignment with NIST CSF functions and how Vault’s capabilities help in meeting these criteri as we’ll see in the upcoming sections.
The Role of NIST CSF: Structuring Cybersecurity Measures
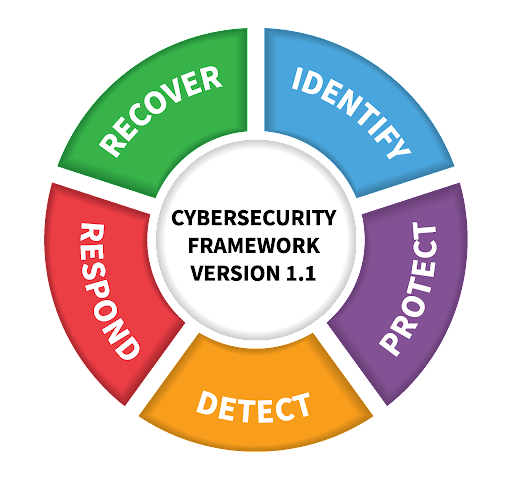
Since this content was prepared, NIST has launched CSF 2.0
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) provides a structured approach to managing cybersecurity risks through five core functions: Identify, Protect, Detect, Respond, and Recover. This framework helps organizations like Little Big Mining Co. establish and maintain a comprehensive cybersecurity posture.
- Identify: Establishes the foundation for effective cybersecurity management by understanding assets, risks, and vulnerabilities.
- Protect: Implements safeguards to ensure the confidentiality, integrity, and availability of critical assets and data.
- Detect: Develops capabilities to identify cybersecurity events promptly and initiate appropriate responses.
- Respond: Takes action to contain incidents, mitigate their impact, and restore normal operations.
- Recover: Implements strategies to restore systems and processes after a cybersecurity incident, ensuring business continuity.
Next, we’ll take a look at how SOC2 and NIST CSF relate to one another and how this relation can be used to highlight tooling requirements.
Vault: Empowering Edge Security and Compliance
As Little Big Mining Co. navigates the intricacies of compliance and security in edge computing, HashiCorp Vault emerges as a pivotal ally. Vault’s array of features, particularly its renowned Public Key Infrastructure (PKI) engine, directly addresses the multifaceted challenges of safeguarding data while ensuring adherence to rigorous standards like SOC 2.
Identity-Based Authorization: Vault’s identity-based authorization mechanism offers a nuanced control layer over access to sensitive information. By associating access permissions with individual identities, Little Big Mining Co. can implement the principle of least privilege effectively, substantially reducing the risk of unauthorized access. This approach resonates with the SOC 2 control for security, demonstrating Vault’s capacity to meet and exceed compliance expectations.
Certificate Management: Vault’s PKI engine simplifies the complexities of certificate management — from issuance to renewal and revocation. This ensures the secure management of cryptographic keys and digital certificates, a cornerstone for maintaining the integrity and confidentiality of data in transit and at rest. The streamlined process not only mitigates the risk of data breaches but also aligns with SOC 2’s processing integrity and confidentiality criteria.
Audit Logging: With Vault’s comprehensive audit logging capabilities, every interaction with the PKI engine is meticulously recorded. This visibility is instrumental for compliance audits and proactive security monitoring, allowing Little Big Mining Co. to trace every certificate issuance, renewal, and revocation. Such detailed logging supports the SOC 2 availability control by ensuring that systems and data are reliably accessible and secure, fostering an environment of transparency and trust.
Certificate Lifecycle Management: The automation of certificate lifecycle management by Vault addresses a critical aspect of cybersecurity hygiene. It minimizes human error and operational overhead in managing the lifecycle of cryptographic keys and certificates. This automation is particularly relevant for adhering to the SOC 2 privacy principle, as it ensures personal information is protected throughout the data lifecycle, enhancing the overall security posture and compliance.
In a real-world application, Little Big Mining Co. leverages Vault centrally to manage identities and issue certificates, ensuring that services running on local Kubernetes clusters at remote sites operate within a secure and compliant framework. This centralized approach enables them to maintain a comprehensive audit log, offering granular visibility into access and authentication events across their distributed infrastructure. Such a strategy not only bolsters their security posture but also aligns with their compliance objectives by ensuring that every service is authorized and operates under stringent security protocols.
Keeping Current with Vault: Vault continues to evolve, with recent updates enhancing its capabilities in areas such as scalable identity management and advanced encryption handling. These developments ensure that organizations like Little Big Mining Co. are equipped with the latest tools to address emerging security threats and compliance requirements.
Bridging Frameworks with Practical Tools: The SOC 2, NIST CSF, and Vault Mapping
Now that we’ve outlined the SOC 2 controls, NIST CSF functions, and introduced Vault’s capabilities, it’s time to bring these elements together. The next part of our discussion features a table that maps SOC 2 controls to NIST CSF functions, with a column showing how Vault supports each requirement. This table isn’t just for show; it’s a practical tool aimed at helping organizations like Little Big Mining Co. use Vault to meet SOC 2 and NIST CSF standards, enhancing their compliance and security framework.
| SOC 2 Control | NIST CSF Function | Vault Capability |
|---|---|---|
| Security |
|
|
| Availability |
|
|
| Processing Integrity |
|
|
| Confidentiality |
|
|
| Privacy |
|
|
We present a table that directly connects SOC 2 controls with NIST CSF functions and links them to Vault’s features that aid in meeting these criteria. This straightforward mapping is designed to help organizations translate compliance and security guidelines into concrete actions, using Vault to navigate the requirements of SOC 2 and NIST CSF effectively.
By demonstrating how Vault’s features align with recognized compliance standards, this table serves as a roadmap for organizations looking to bolster their security and compliance strategies in the realm of edge computing.
Conclusion: Charting a Course Through Compliance and Security
As we’ve seen through the journey of Little Big Mining Co., the path to securing edge computing environments and achieving compliance with standards like SOC2 and NIST CSF is complex but navigable. The strategic decision to pursue SOC2 certification, underpinned by the comprehensive guidelines of the NIST CSF, represents more than just a commitment to security; it’s a foundational step towards building trust, enhancing operational resilience, and fostering business growth in the digital age.
In this rapidly evolving landscape, tools like HashiCorp Vault are not just beneficial; they are essential. Vault’s capabilities in identity-based authorization, certificate management, audit logging, and certificate lifecycle management offer tangible solutions to the abstract challenges of compliance and security. The detailed mapping of SOC2 controls to NIST CSF functions, further illuminated by Vault’s supporting features, provides a blueprint for organizations embarking on their compliance journey.
Ultimately, the story of Little Big Mining Co. is a microcosm of the broader narrative unfolding across industries worldwide. As companies navigate the complexities of digital transformation, the principles of robust cybersecurity measures, compliance adherence, and strategic tool selection remain paramount. By embracing these principles, organizations can not only safeguard their assets and data but also unlock new opportunities for innovation and growth.
Let the journey of Little Big Mining Co. inspire your own path through the wilderness of edge computing. With the right strategies, tools, and frameworks in place, navigating the challenges of compliance and security becomes not just feasible, but a strategic advantage in the digital frontier.
I previously had delivered these ideas in a presentation at HashiTalks 2024, you can catch the original talk here